A look at how the focus of modern smart card applications, especially in the electronic identity card landscape, has shifted from an approach purely driven by ‘forgery protection’ to a citizen value-centric approach
by Thomas Röder, NXP
 Smart card solutions have seen a broad adoption within the last two decades. Today, billions of smart cards provide easy access to public transportation, are used as secure tokens for payment solutions or protect the card holder’s personal identity in electronic identity documents, and facilitate government services.
Smart card solutions have seen a broad adoption within the last two decades. Today, billions of smart cards provide easy access to public transportation, are used as secure tokens for payment solutions or protect the card holder’s personal identity in electronic identity documents, and facilitate government services.
The first smart card implementations were contact-based. Contactless smart card solutions were developed mainly by Philips Semiconductors in the early 90s when Philips launched its first Mifare products for a variety of ticketing applications such as ski lifts and mass transit as well as generic building access control applications. Since then, contactless smart cards have been adopted in many applications. However, ticketing, transportation applications and access applications in general are still dominating. Billions of such smart cards have been deployed on a worldwide base. Another high volume contactless security token solution is car immobilizers based on contactless ICs. These devices have helped to decrease the number of car thefts significantly within the last 15 years.
The German National eID – one of the most sophisticated national eID implementations deployed today – is based on a fully featured contactless smart card IC. The lifetime requirement of 10 years for the eID smart card within this project can only be fulfilled by a contactless solution. Dedicated secure communication protocols secure the contactless data transmission. As such, contactless smart card solutions can be implemented in such ways that the highest security requirements can be met. The same principles apply as for every kind of secure key exchange and secure messaging schemes over open networks. An end-to-end security mechanism needs to be properly applied to realize a highly secure implementation.
Internet
The Internet changed the way we work, communicate, correspond, consume and spend our leisure time. A face to face society has turned into a virtual society. One of the main challenges within such
a connected world is to provide instruments that enable users to distinguish between real and faked identities, potential business partners or information. Identification no longer means physical presence – as such, secure identification has turned into secure authentication. Schemes to authenticate and correspond in a legally binding manner are fundamental to capitalizing on the opportunities afforded by the most powerful media ever created.
The authenticity of an identity needs to be proven using credentials uniquely connected to a clearly defined entity – which could be a person or any other legal entity – and which can be used solely by this identity. Thus, credentials need to be stored and transmitted secretly. Secure containers able to store secrets and cryptographic communication tools are required to serve those requirements. PC platforms do not comply with those requirements at all, but secure smart card solutions are designed to meet them perfectly. They provide a highly secure platform where confidential data can be stored securely and they come in a portable format ready to be used wherever it is required. As such, they provide real end user value.
There is a fundamental difference between PC platforms and smart cards: smart cards cannot be easily compromised by viruses or Trojan horses, while PC platforms have a high vulnerability with respect to malware. There are many mechanisms implemented that protect secret data on smart cards, and the latest high security smart card solutions – typically used within the applications described in this article – can withstand all known attack schemes without confidential data being disclosed. Independent certification bodies are in place to confirm this level of protection exists before a security certificate for a dedicated smart card application is issued. And because technology evolves on both sides, with attackers getting access to more powerful tools, security technology is also constantly being improved – products are constantly updated to comply with the latest security demands.
Modern applications
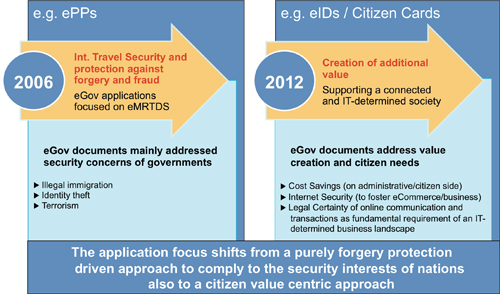
The application focus of modern smart card applications, especially in the electronic identity card landscape, has shifted from an approach purely driven by ‘forgery protection’ to a citizen value- centric approach, as illustrated by Figure 1. This is also true for smart card applications in the payment, access and transportation industry. The creation of user value is key. Contactless smart card solutions are the perfect vehicle for this, as they offer maximum convenience during usage and are compliant with all levels of security requirements.
Secure vehicles
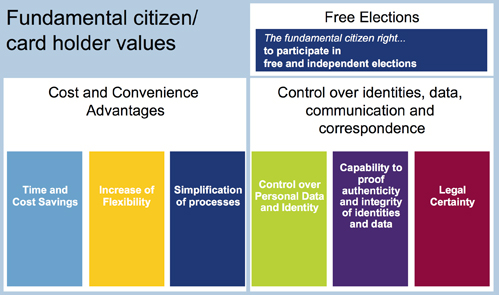
Beside the need to comply with the highest security requirements, maximization of user value is increasingly dominating the identity card schemes. A major feature of the latest national electronic identity card implementations is that these devices do not just support the physical identification of a person. They are multi-application devices offering additional features that enable card holders to securely navigate through a connected world. Those features, which will be discussed later in this article, provide fundamental user values, as listed in figure 2.
Time and cost
While online services are widespread, there are still many services which require face to face (F2F) contact, as secure identification is required to provide the service. This is true for many governmental or administrative services such as address change, tax declaration or car registration. It is also true for commercial services such as opening a bank account or applying for insurance. Face to face contact means: `Time expenditure
`Travel, which is directly related to cost
`Fees to be paid, as there is also a significant cost connected to F2F services on the service provider’s sid
ID cards with a secure online authentication function based on strong cryptography provide proven mechanisms to securely identify persons over open networks. Thus, services which can only be provided to securely identified persons can also be offered online. Cost and time advantages are significant on both the citizen and service provider sides – it means fewer kiosks, less staff and faster response times.
Increased flexibility
Spatial limitations are no longer a concern if secure authentication schemes enable the provision of online services with strong identification requirements. Time critical tasks can be performed while in the office, abroad on a business trip or on vacation. Citizens need no longer depend on the opening hours of the service provider: internet access is available 24/7.
Simplification
Here is a real world example: the simplification of processes has been the main contributor to the success of health cards introduced in the 90s. With no need to fill in application forms any longer, client management has been significantly simplified, while cost savings and faster response times have also been achieved.
In terms of electronic identity cards offering secure online authentication, processes can be simplified if a person can authenticate reliably based on an official electronic identity. There is no need for a number of security tokens for every special service, each requiring a PIN or password. One official electronic identity can be utilized to access all important online services: administrative/eGovernment services, ebanking, transportation or health/medical services. Secure Single Sign On applications can be easily implemented. As such, one card provides access to a number of important applications, increasing the convenience level and user acceptance significantly.
Control over personal data
 Data exchange during an online session might contain a lot of personal data which can be easily spied upon or altered when transmitted over open networks such as the internet. Secure protocol layers such as secure socket layer (SSL), which establish a secure end-to-end messaging channel between the connected parties, can prevent third parties from eavesdropping. However, even when personal data has been provided intentionally by a user over a secured messaging channel, it might be later abused to steal the user’s identity. Secure smart card solutions can provide mechanisms to significantly increase control over personal identities and data. The value of this to the user cannot be overestimated. The damage potential is huge when a personal identity is stolen and abused.
Data exchange during an online session might contain a lot of personal data which can be easily spied upon or altered when transmitted over open networks such as the internet. Secure protocol layers such as secure socket layer (SSL), which establish a secure end-to-end messaging channel between the connected parties, can prevent third parties from eavesdropping. However, even when personal data has been provided intentionally by a user over a secured messaging channel, it might be later abused to steal the user’s identity. Secure smart card solutions can provide mechanisms to significantly increase control over personal identities and data. The value of this to the user cannot be overestimated. The damage potential is huge when a personal identity is stolen and abused.
There are even mechanisms available that enable card holders to authenticate anonymously and securely without disclosing any personal data. This can be a requirement of card holders when entering chat rooms or platforms where they prefer to stay anonymous. As such, privacy concerns can also be fully addressed. Citizen-friendly implementations of electronic identity solutions complying with data privacy protection requirements are possible, which means that “Big Brother” doesn’t have to be around every corner.
Another feature and a very good example of minimizing the disclosure of personal data is the “age verification” feature. Many online services require age verification, typically connected to disclosure of all personal data (name, address, birth date etc). An age verification function on the ID card is able to simply confirm whether a card holder meets the minimum age requirement without disclosing any further personal data. Additionally, children can be reliably excluded from accessing restricted services.
Authenticity and integrity
The ability to prove the authenticity of identities such as potential business partners or chat partners, plus the ability to ensure the authenticity and integrity of data (e.g. when performing financial transactions) are vital in an increasingly virtual world. “What you see is what I am” or “what you see is what you get” is no longer always the case. Web pages with fake identities have flooded the internet and are a real threat – just think of the many incidents of vulnerable youngsters being misled by predatory adults hiding behind false identities in chat rooms; or the huge number of phishing attacks, where criminals attempt to obtain PINs or TANs to access to bank accounts. The damage due to phishing attacks has been roughly 17M Euro in Germany in 2010 according to the Bitkom and German Bundeskriminalamt.
 Secure smart card solutions support mechanisms allowing both parties connected via an open network to securely and reliably identify each other via a mutual authentication scheme. In parallel,
Secure smart card solutions support mechanisms allowing both parties connected via an open network to securely and reliably identify each other via a mutual authentication scheme. In parallel,
a secure messaging channel is established to protect the connection from eavesdropping. Based on such solutions, trust can be established between the partners. Personal and confidential data can be exchanged while the authenticity and integrity of identities and data can also be assured.
The German National eID (neuer deutscher Personalausweis) implementation is strongly focusing on satisfying the needs described above. This eGovernment document comes with online authentication functionality where privacy, data minimization and data self-determination requirements have been fully considered. Before any personal data is sent by the smart card during an online authentication procedure, the card holder needs to approve whether he is willing to provide any personal data and if yes, what subset of data, stored on the card, he is willing to disclose. A mutual authentication protocol ensures whether the server/terminal the user is connected to is based on an officially approved identity and has the correct access rights to the personal data stored on the identity card.
Such a scheme can be realized based on smart card verifiable certificates that the server needs to provide during the mutual authentication procedure. The smart card is able to verify whether the certificate is valid and has been issued by an official certification authority. As such, the cardholder can be sure that the authenticity of the service provider – which could be an online shop – has been officially validated and approved. The effort to install and maintain a system able to provide such functionality is significant. A complex multi-level public key infrastructure needs to be in place.
Future platform
A modern society which increasingly relies on online services requires technology that can provide
a ’personal secure identity’. It is a fundamental prerequisite for an open and secure ICT-connected society where commercial and public businesses and services can prosper. Smart card technology has proven over time to be an adequate platform to host such a personal identity.