A study on why smart cards are the best bet to secure enterprise, healthcare, financial, and transit organizations’ IT Systems for identity management and security, offering new ways to strongly authenticate identities prior to granting access to computer networks, systems and applications
by Randy Vanderhoof Smart Card Alliance
 Smart card technology has advanced over the last 30 years: storage and processing capabilities are improved, security has been enhanced, the management software has matured, contactless technologies are available, and multiple applications can now be integrated on a card. Smart cards now support a variety of the logical access applications used by organizations, including network logon, one-time passwords (OTPs), virtual private network (VPN) authentication, e-mail and data encryption, digital signatures, enterprise single sign-on, secure wireless network logon, and biometric authentication. Today, smart cards can play an essential role in the security backbone of an organization’s identity management architecture, supporting the strong authentication required to validate individuals accessing networked resources and providing a critical first step in protecting against intruders.
Smart card technology has advanced over the last 30 years: storage and processing capabilities are improved, security has been enhanced, the management software has matured, contactless technologies are available, and multiple applications can now be integrated on a card. Smart cards now support a variety of the logical access applications used by organizations, including network logon, one-time passwords (OTPs), virtual private network (VPN) authentication, e-mail and data encryption, digital signatures, enterprise single sign-on, secure wireless network logon, and biometric authentication. Today, smart cards can play an essential role in the security backbone of an organization’s identity management architecture, supporting the strong authentication required to validate individuals accessing networked resources and providing a critical first step in protecting against intruders.
Authentication
In general, authentication is the process by which something is shown to be genuine. The term is applied to the identity of a person (though it can also be extended to things) and, by extension, to the items used to prove that identity to an electronic system, such as background documents, user name-password combinations, smart cards, or biometric data.
The authentication method used and the extent to which it is applied depends on the subject being examined. For example, different measures are employed to authenticate a $1 bill as opposed to a bill of a much higher denomination. Similarly, a different method is used to authenticate someone who is requesting access to a product technical support web site as opposed to someone accessing secure government or military networks.
Where minimal security is required (such as on a home computer that is not connected to the Internet), a simple logon name may be sufficient. Requiring authentication, such as a personal identification number (PIN) or password, adds a level of protection. This combination provides minimal authentication and can be supplemented or replaced by requiring other authentication tokens, such as digital certificates, hardware-based authentication tokens, or biometric data.
The strength of any authentication process depends on both the quality and diversity of its constituent parts. To build greater integrity into a solution, the authentication methods should employ complementary mechanisms. Historically, these mechanisms have included something a person knows (a password), possesses (an object), or is inherent to their physiology or behavior (a biometric factor).1 The concepts of uniqueness and secrecy are very important in this context. Although location data and knowledge-based authentication can limit the potential for fraud within a system, as currently implemented they provide only a limited degree of uniqueness and secrecy, respectively.
Drivers
Changes in the business environment can represent strong drivers for IT processes and for implementing stronger authentication. The increasing number and popularity of e-commerce business applications, the migration to cloud-based systems, critical requirements by employees and customers for remote information access, and the move to bring-your-own-device implementations, all argue for ensuring that strong authentication is in place for every transaction. Protecting both an organization’s information and the customer’s information is critical, for a number of reasons.
Numerous businesses are currently trying to comply with new or changing regulatory mandates, such as the Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley Act, Gramm-Leach-Bliley Act, Visa Waiver Program, or International Civil Aviation Organization Machine-Readable Travel Documents specifications. Many of these mandates affect policymakers as well as IT departments. Stronger authentication methods can help address mandated requirements for access and audit trails.
Many organizations or their business partners have suffered from a security breach, or an audit has uncovered vulnerabilities. Such events can be costly and unpleasant, but they can provide the motivation to justify implementing stronger security measures. Analyzing these events for weaknesses in current authentication procedures permits organizations to apply stronger authentication methods to their current systems.
Many organizations are implementing centralized identity management systems, moving to cloud-based solutions or implementing bring-your-own-device strategies. This IT infrastructure migration provides opportunities for organizations to also implement stronger authentication processes to protect critical business resources and address governance, risk management and compliance objectives.
Identity proofing
 Identity proofing is the method by which an individual proves their identity to an identity provider and the identity credential issuer. The identity proofing process requires significant human involvement and takes a long time. Therefore, rather than repeating the effort for each logical or physical access attempt, the relying party issues a credential that links to a digital identity for the individual and that can be electronically validated for future access requests.
Identity proofing is the method by which an individual proves their identity to an identity provider and the identity credential issuer. The identity proofing process requires significant human involvement and takes a long time. Therefore, rather than repeating the effort for each logical or physical access attempt, the relying party issues a credential that links to a digital identity for the individual and that can be electronically validated for future access requests.
An identity proofing process of some kind occurs millions of times every day for people across the globe. Throughout the course of their lives, most people hold multiple identity credentials, each with a different purpose and a different renewal schedule. The certainty with which this identity must be proven is determined by the relying party and is likely to be related to the risk of allowing access inappropriately and the threat of attacks on the identity proofing process. Commonly the identity proofing process can include the following activities:
- presentation of identity documentation (e.g., birth certificate, passport)
- verification of documentation (where appropriate)
- confirmation of approval to access information or facility
- positive vetting of the individual’s identity (i.e., background check), if a very high level of assurance is required
- biometric data capture (either for identity proofing, duplicate registration rejection, or inclusion as an authentication token)
- issuance of the credential (frequently as a badge or hardware token, such as a smart card)
- personalization and activation with creation of a PIN or password.
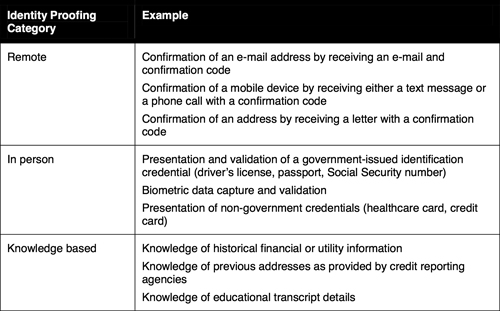
Identity proofing and the process by which an identity credential is issued are the cornerstones of strong authentication. Using more than one identity proofing procedure increases the level of assurance that a person is who that person is claiming to be. Table 1 lists examples of identity proofing procedures used in the government, financial, higher education, and corporate sectors.
Derived credential
A ‘derived credential’ is a credential that is issued based on a previously issued credential, created for use in a different application and/or in different form factors.
A derived credential in a smart mobile device could be issued upon presentation and validation of a PIV card. This option requires the PIV card to be presented to a mobile device manager (MDM) which then assigns the derived credential to a smart mobile device, a new logical credential being stored within the mobile device. The credential would typically be placed on a secure element within the mobile device (e.g., a secure element in the UICC/SIM, in a microSD card or in a separate embedded chip).
The derived credential differs from the PIV card in that it may not necessarily be used where PIV cards are normally accepted; it is independently revocable; any associated card authentication key (CAK) identify it as mobile; and it could imply different levels of security and authority. The derived credential would also be revoked by default when the PIV credential from which it was derived is revoked.
In addition to mobile devices, derived credentials could take the form of other smart cards and tokens for use on laptops and desktops, and for Web access. Derived credentials are in the process of being standardized by NIST. FIPS 201-2 refers to a future NIST special publication, SP 800-157 (Guidelines for Personal Identity Verification (PIV) Derived Credentials), that will provide guidelines on PIV derived credentials.
Authentication factors confirm that a person is who that person claims to be. There are three standard categories of authentication factors:
- an ownership factor, or something you have
- a knowledge factor, or something you know
- an inherence factor, or something you are
Authentication tokens
The most commonly used authentication token is the password. Someone provides a user name and password and requests access. A computer system compares the user name and password combination to stored information. An electronic response grants or denies access based on the results of this comparison.
Passwords have been widely recognized as a weak form of authentication5, with increasing amounts of password theft, either directly from the owner, through network intrusion, or through unauthorized database access. Passwords are typically controlled by the password owner, who can select easily guessed passwords, share passwords with others, write passwords down, use the same password to access multiple systems, or inadvertently compromise the password as the result of a phishing attack. In addition, storing password data on corporate networks introduces additional vulnerability should attackers gain network access.
Private enterprises and government agencies are moving to replace simple passwords with stronger, multi-factor authentication that strengthens information security, responds to market and regulatory conditions, and lowers support costs.
Knowledge based authentication (KBA) uses personal information to validate someone’s identity electronically. KBA can be used to identify someone accessing an information system, service, or Web site. KBA can be deployed statically or dynamically. Static KBA implementations generally use various combinations of stored information that someone provided earlier. The implementation can obtain the information from one or multiple systems, smart cards, and services. However, all shared information to be used for identity verification must have been recorded earlier (i.e., sensitive data that is shared prior to use). This shared personal information is sometimes referred to as “shared secrets.” Dynamic KBA implementations can enhance the level of verification, because they do not rely on prearranged shared information for authentication. Instead, the system can use information acquired on the fly, from (for example) smart cards, public records, marketing data, or credit reports. Likewise, dynamic KBA implementations can change shared information rules dynamically. The choice of a static or dynamic KBA implementation should be made with proper due diligence.
Public key cryptography
Public key cryptography (also known as asymmetric key cryptography) encrypts information using mathematically related pairs of cryptographic keys. One key in the pair is used to encrypt information; the information can then only by decrypted using the other key. The key pairs are obtained from a trusted authority and used to exchange data securely and privately.
Each key pair comprises a public key and a private key. The public key is used to encrypt confidential information. The private key authenticates the key holder and decrypts information that has been encrypted using the public key. The private key must be kept secret. The recipient using the private key can therefore be certain that the information the key is able to decrypt was intended for them, and the sender can be certain that only the holder of the private key can decrypt the information sent.
Smart card technology provides a portable platform where the asymmetric key pair can be generated and securely stored in the card. Private key cryptographic functions are performed on the card and the key cannot be revealed, exported or copied. In addition, a smart card is capable of binding the card to the card owner and the public key to the card. As another benefit, several laptop manufacturers are offering smart card readers as a standard feature in their products.
 Certificate-based smart cards using PKI can provide strong multi-factor authentication in a traditional ID card form factor. Smart cards with two-factor authentication provide high assurance identification and authentication to applications and networks where security is critical. Smart cards offer a single solution for strong authentication and logical access applications including network access, remote access, password management, network logon, as well as corporate ID badges for identification, physical access control, and payment systems. Further, certificate-based smart cards can achieve the highest security standards including FIPS 140-2 and Common Criteria, and enable compliance with other security regulations and guidance.
Certificate-based smart cards using PKI can provide strong multi-factor authentication in a traditional ID card form factor. Smart cards with two-factor authentication provide high assurance identification and authentication to applications and networks where security is critical. Smart cards offer a single solution for strong authentication and logical access applications including network access, remote access, password management, network logon, as well as corporate ID badges for identification, physical access control, and payment systems. Further, certificate-based smart cards can achieve the highest security standards including FIPS 140-2 and Common Criteria, and enable compliance with other security regulations and guidance.
One-time passwords
A one-time password (OTP) can combine the factors of something a person knows (e.g., a passphrase) and something a person has (e.g., possession of a token). An OTP displays a single use password. Each time a person authenticates to a system, a different password is generated and used, after which that password is no longer valid. The password is computed either by software on the computer system or by OTP hardware tokens in the person’s possession that are coordinated through a trusted system. One common implementation model is for the password to be generated by a portable device such as a USB device, smart display card, or mobile phone.
OTPs were developed to combat the problems encountered in using personally-selected static passwords and managing password security policy. The key to a successful OTP solution is that each OTP is different from the previous one, and the sequence of OTPs cannot be guessed based on observation of previous passwords. These methods are designed to protect against “man in the middle” and other attacks.
Biometrics
Biometric factors, or something you are, are an important component of multi-factor authentication. Biometrics bind an individual to an asserted identity both during the identity credential registration process and during the authentication event.
Strong authentication currently has no precise definition; it is not a strictly mathematical concept with purely quantitative measurements, but rather a qualitative measure with a relative scale. For example, the government’s Personal Identity Verification (PIV) smart card program outlines the following levels of authentication assurance:
- some confidence: a basic degree of assurance in the identity of the cardholder
- high confidence: a strong degree of assurance in the identity of the cardholder
- very high confidence: a very strong degree of assurance in the identity of the cardholder.
Smart Cards
Smart cards can significantly increase the security of a person’s identity credentials. The credentials can be permanently stored on the card, which is in the person’s possession. In addition, sophisticated attacks on smart cards are time-consuming and expensive, and the attacker must have physical possession of the card.
If a person’s smart card is missing, it is likely that the person will report it, and the card can be revoked and re-provisioned before an attack can succeed. When credentials are stored on someone’s computer, that person may never know that they have been stolen.
Smart cards are typically used to enable two-factor authentication, incorporating something you have (the smart card) and something you know (typically a PIN that activates the card’s cryptographic functions). Taking control of a person’s digital identity requires both stealing the smart card and guessing the PIN. Cardholders know very quickly when a card is stolen and can contact an authority to report the stolen credentials. In addition, too many incorrect PIN guesses can lock the card.
Smart card technology also supports the addition of biometric tokens (something you are), enabling three-factor authentication.
As an alternative, the biometric can replace the PIN, which strengthens security while increasing convenience. Adding biometric authentication to an access control solution is easy, because the smart card can store the cardholder’s biometric template and perform the processing required to check for a match. No back-end database is required. Storing the credentials for accessing an application securely on a smart card, protected by the cardholder’s biometric data, provides an organization with biometric security without having to involve back-end applications.
Smart cards offer the following advantages:
- secure password file storage
- ability to generate asymmetric key pairs and store PKI certificates securely
- secure symmetric key storage
- secure OTP seed storage
- secure biometric template storage.